The Making of Badblood
Posted on January 27, 2020 by David Rowe ‐ 3 min read

 Last year I released my Active Directory script to deploy a huge part of Microsoft ESAE direct into any domain “Create Tiers.” It’s sexy. Or at least I think it’s sexy. In the information security world, it’s defensive; blue team. So… it isn’t sexy.
Last year I released my Active Directory script to deploy a huge part of Microsoft ESAE direct into any domain “Create Tiers.” It’s sexy. Or at least I think it’s sexy. In the information security world, it’s defensive; blue team. So… it isn’t sexy.
I have a difference in opinion on what people might consider “sexy”. I live by the motto, “if you have to do it twice, automate it”. To me, automation is sexy…
I learned if you can find someone that can orchestrate common tasks, he or she is an incredible coworker. But I can’t find anyone who would consider properly handling updates, reboots, or patches “sexy.” Is defensive scripting ever considered “sexy?”
Well, I think it’s sexy. So what? Is that wrong?
When I’ve been forced to perform common jobs in larger than life Active Directory environments, what did I do? I orchestrated it. With coffee and code. First coffee. Then code. If I ever did code first I often did; code, coffee, then a bugged release led me to code again.
So I coffee then code. It’s faster that way. But I digress.
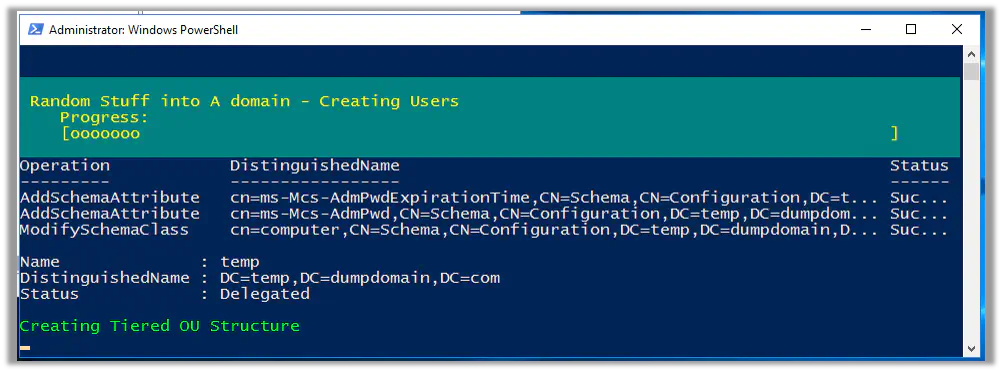
Months after my Tiering script was released, it still didn’t get much attention. It seemed people wanted chaos instead of organization. As time slipped by I heard time and time again, “Is there any way to make a test Active Directory?” Or, “I want to test users, groups permissions. All of it. I want to learn it. How can I learn?” This wasn’t just a one time request. Every month I heard it. Maybe even twice a month. “I want a domain. I want to learn Bloodhound!” Was the battle cry. “Bloodhound is sexy!” (I admit. I made up that last chant and threw it into the fray.)
…In case you didn’t know already, Bloodhound is sexy. Not just because it’s red team, because it’s blue team too. Purple tools = sexy.
I knew I could secure a domain with the click of a button, but who likes a clean house? Who wants all the dirty laundry put away in little baskets? The floors swept and mopped? The coats all handing up by the door and the shoes put away? Not the security world! Clean isn’t sexy! Dirty is sexy! Let’s make the house dirty!
Let’s open all the closets! Let’s air the dirty laundry. Heck, let’s find shoe baskets put them on the stairs and stack jackets in them! No, stacking is too neat. Let’s crumble a jacket and throw it in the basket then we’ll put a dirty take-out container on top of it.
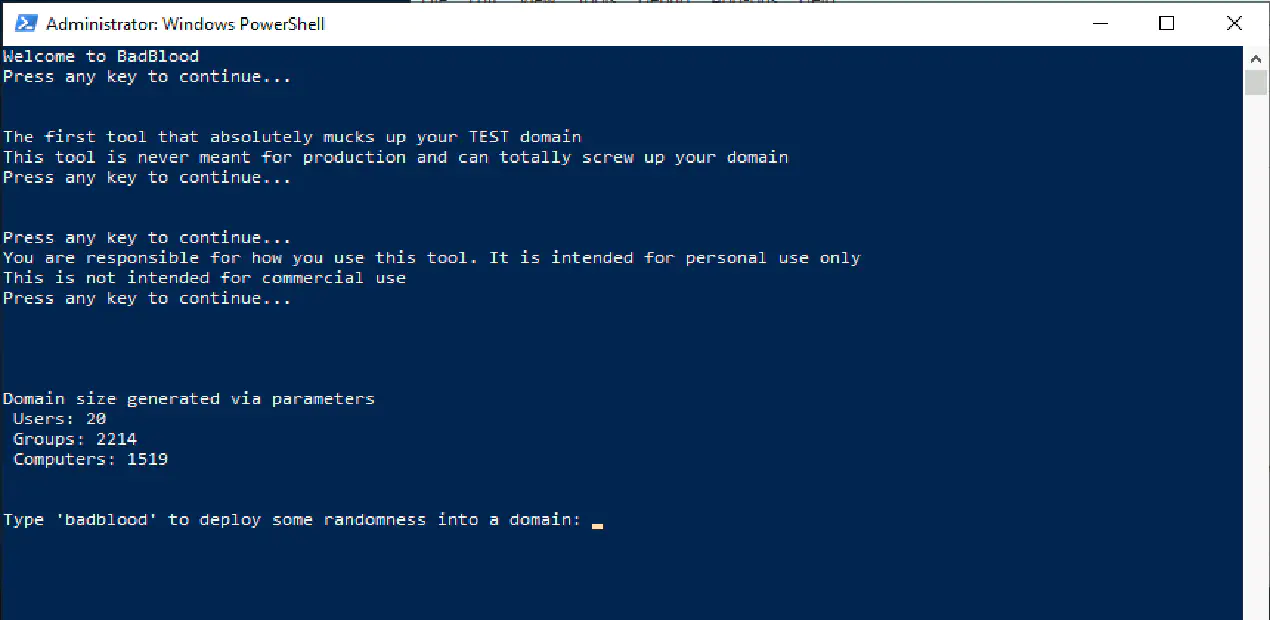
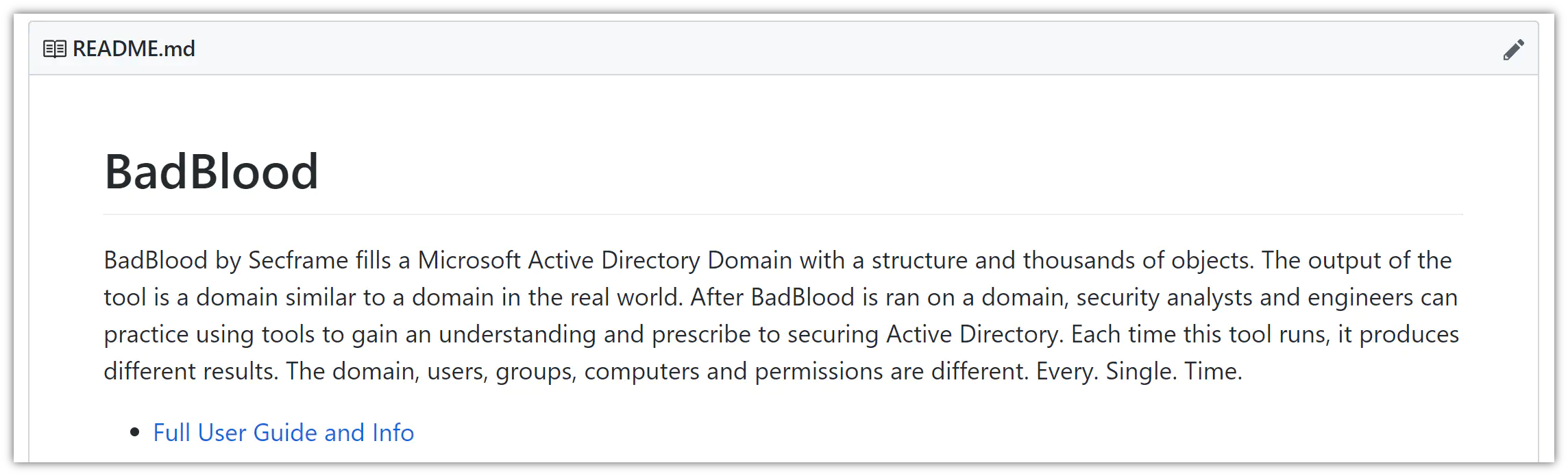
So here comes BadBlood.

Take the create tiers script and reverse it. Take creation scripts and asset management scripts, and slap them on top. Take the permissions tiers script and put randomizers into it.
Put OUs everywhere. Users in the most random of places. Groups wherever they decide to go. Then put those groups in groups and those users in groups. Then give the groups and users ways to make changes or do things to other groups or users. It’s a madhouse in here!
Users in the most random places! Groups wherever they decide to go!
“That’s fun! That’s dirty. That’s security. That’s sexy!” And just by reversing my tiering code and adding a randomizer on it…I learned it’s “sexy.”
In this BadBlood blog series I’ll jump into bits and pieces of a domain generated by BadBlood and walk you through some Active Directory configuration attack vectors and how a security audit remediation can remove those attack vectors. Stay tuned.